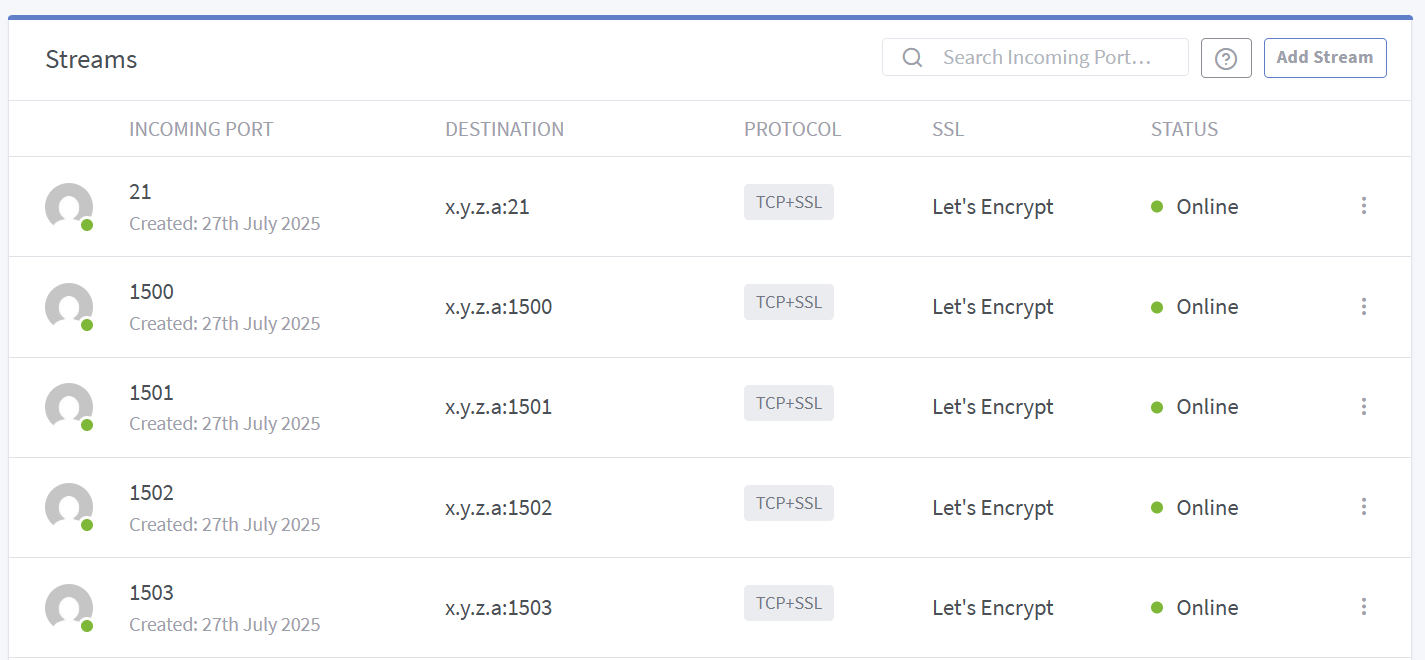
When you run an FTP server in 2025, like a surviving dinosaur, and you have the presence of mind to add a TLS layer, you may find yourself puzzled by the lack of support for certificate renewal in commercial FTP server software. The idea of reverse proxying the FTP server makes sense, but FTP likesContinue reading “Reverse proxying FTPS with OpenResty (in Nginx Proxy Manager)”
Category Archives: Write-up
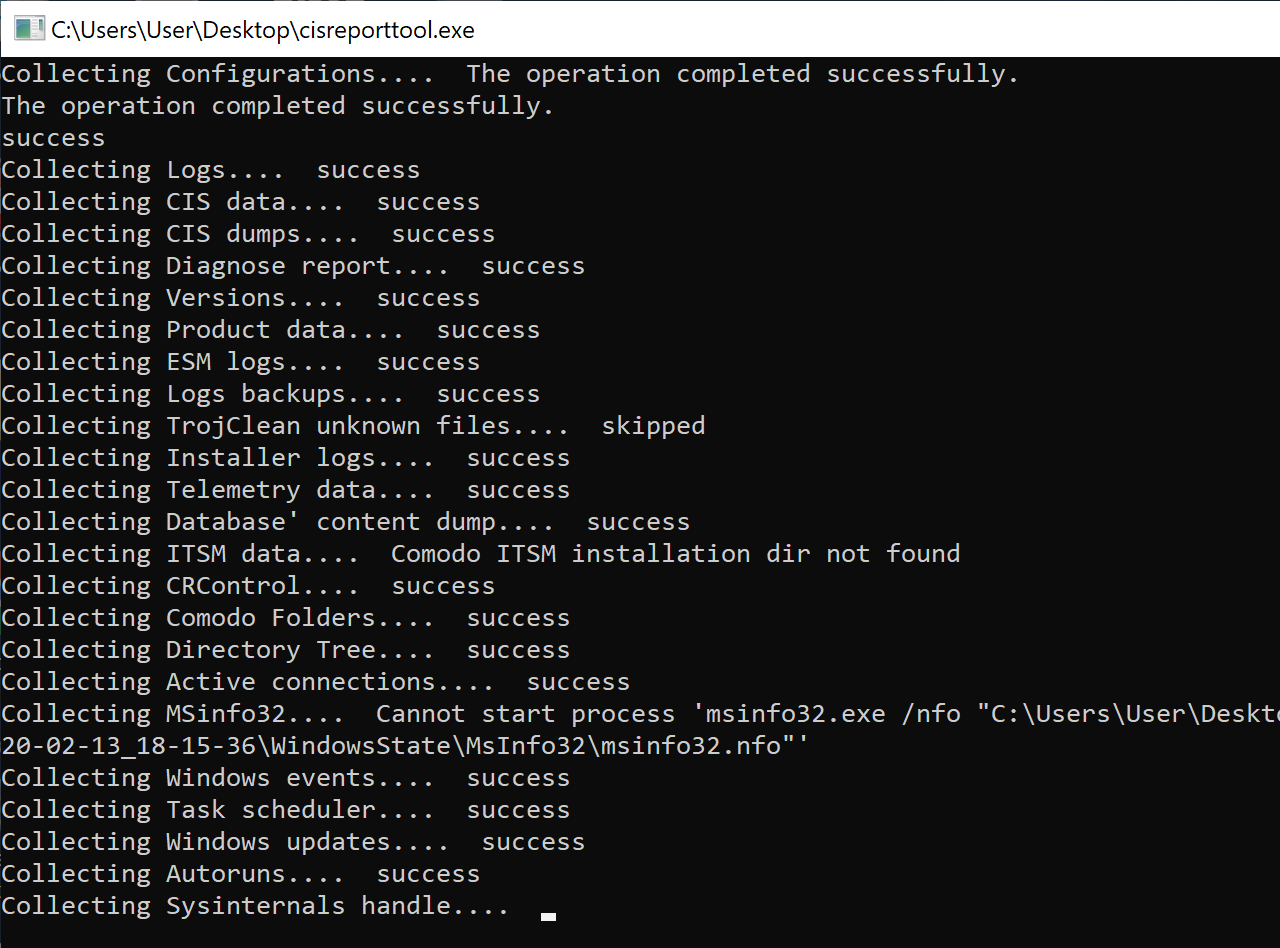
Comodo Report Tool: How Not to Upload System Reports
When troubleshooting a problem with Comodo Firewall with the help of a staff member from the Comodo forum, I found that the tool they asked me to run to gather (extensive) information about my system sends the report to a server via SSH, with hardcoded credentials, next to many other user reports, which are readableContinue reading “Comodo Report Tool: How Not to Upload System Reports”
Upgrading Wireguard Jail from TrueNAS 12 to 13
As TrueNAS 13 reached RELEASE milestone in May 2022 and TrueNAS 12 got abruptly EOL’d shortly after, the usual question stroke me: Should I update now or wait? TrueNAS 13 offered the option to stay on CORE or switch to SCALE. I was attracted by the ability to run containers more easily with SCALE, howeverContinue reading “Upgrading Wireguard Jail from TrueNAS 12 to 13”
NorthSec 2018 CTF – Silent Meeting: Write-up
The Silent Meeting challenge at NorthSec 2018 was worth 20 points with only four flags. For this CTF, 20 points is a lot. And there’s a reason: this challenge went out of the box and literally asked you to recover what music was being played from an audioless video of a loudspeaker, and what didContinue reading “NorthSec 2018 CTF – Silent Meeting: Write-up”
An Analysis of Modified VeraCrypt binaries (Part 3)
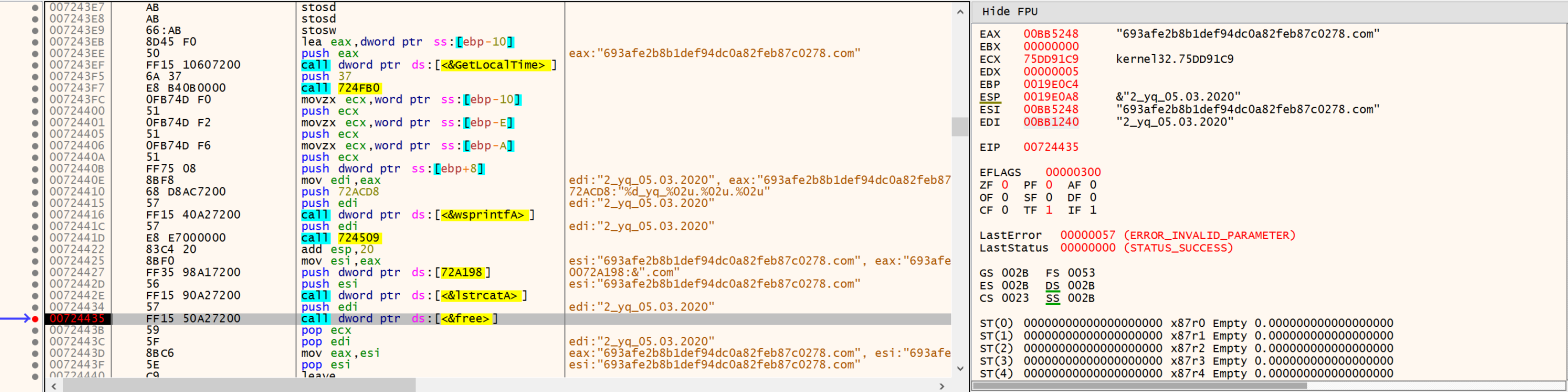
Continuing and finishing on the analysis of the fake VeraCrypt Windows installer distributed on httx://vera-crypt[.]com, I am now reverse-engineering data.dll, which again tries to download another payload from a C2 server. Problem: the server is down. Instead, I’m focusing on recovering an old payload from the same malware family that I decipher from a PCAPContinue reading “An Analysis of Modified VeraCrypt binaries (Part 3)”
An Analysis of Modified VeraCrypt binaries (Part 2)
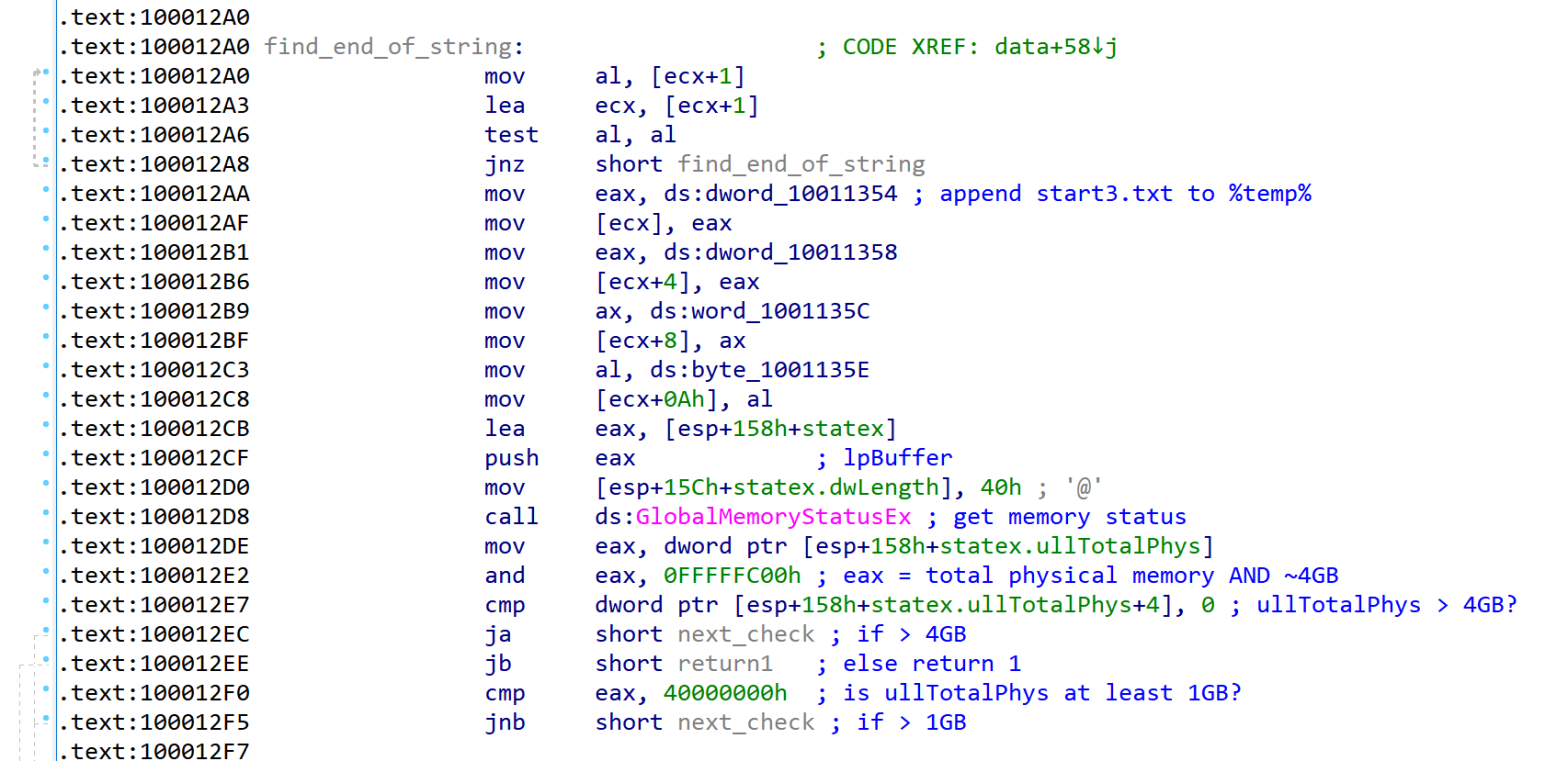
Continuing on the analysis of the fake VeraCrypt Windows installer distributed on httx://vera-crypt[.]com, I am now reverse-engineering the downloaded payloads. Before I can jump to the main functionalities of the malware, I have to go through obfuscation and anti-analysis techniques. This part goes in details into these techniques, and is targeted at above-beginner reverse-engineers. IContinue reading “An Analysis of Modified VeraCrypt binaries (Part 2)”
An Analysis of Modified VeraCrypt binaries (Part 1)
On January 29, 2020, The Twitter account of VeraCrypt (@VeraCrypt_IDRIX) posted a tweet about a fake VeraCrypt website (httx://vera-crypt[.]com) that was distributing modified VeraCrypt installers that are signed with a valid EV code signing certificate from an unknown company. I was intrigued. The fake website was still up, so I decided to look into it.Continue reading “An Analysis of Modified VeraCrypt binaries (Part 1)”